STRONG AUTHENTICATION
CYBERSECURITY CONTEXT
Strong authentication is now part of our daily life. The sophistication of data theft techniques is such that a simple authentication is no longer enough to guarantee optimal protection. Additional security is essential.
Increased use of connected devices and online services raise huge cybersecurity challenges whether for states, businesses or individuals. These new uses store more personal and confidentiels data every day. They break the traditional user security boundaries.
Increasingly sophisticated hacking techniques are emerging: MITM (Man-In-The-Middle), phishing attacks, malware and other cyber attacks that have become more complex. Strengthening access and data security becomes a necessity.
In practice, attackers may have gained access to your account in several ways: a too simple password, the use of the same password on several sites one of which has been hacked…
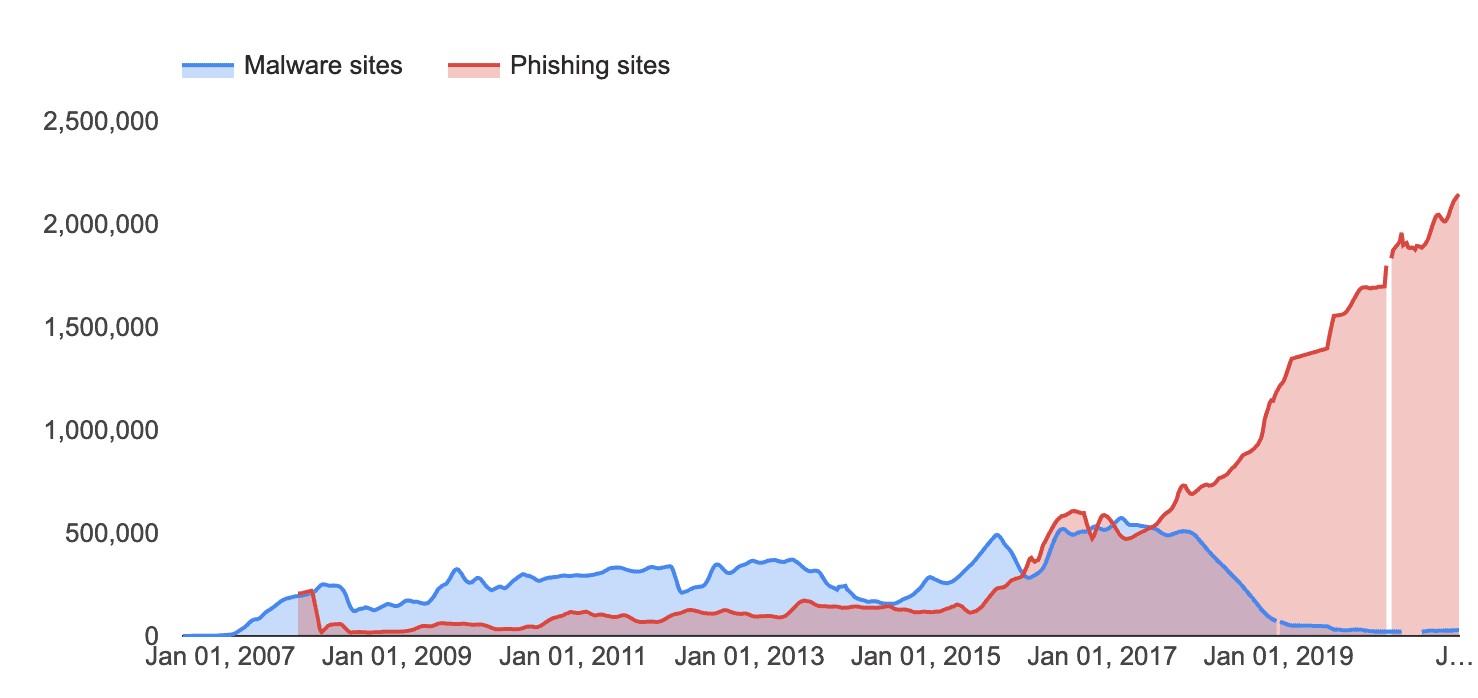
2021 Tessian* research found that employees receive an average of 14 malicious emails per year. Some industries were hit particularly hard, with retail workers receiving an average of 49. CISCO’s 2021 Cybersecurity threat trends report suggests that at least one person clicked a phishing link in around 86% of organizations. The company’s data suggests that phishing accounts for around 90% of data breaches.
 In 2021, RiskIQ estimated that businesses worldwide lose $1,797,945 per minute due to cybercrime—and that the average breach costs a company $7.2 per minute. IBM’s 2021research into the cost of a data breach ranks the causes of data breaches according to the level of costs they impose on businesses.
In 2021, RiskIQ estimated that businesses worldwide lose $1,797,945 per minute due to cybercrime—and that the average breach costs a company $7.2 per minute. IBM’s 2021research into the cost of a data breach ranks the causes of data breaches according to the level of costs they impose on businesses.
Phishing ranks as the second most expensive cause of data breaches—a breach caused by phishing costs businesses an average of $3.92 million, according to IBM. And Business Email Compromise (BEC)—a type of phishing whereby the attackers hijack or spoof a legitimate corporate email account—ranks at number one, costing businesses an average of $5.01 million per breach.
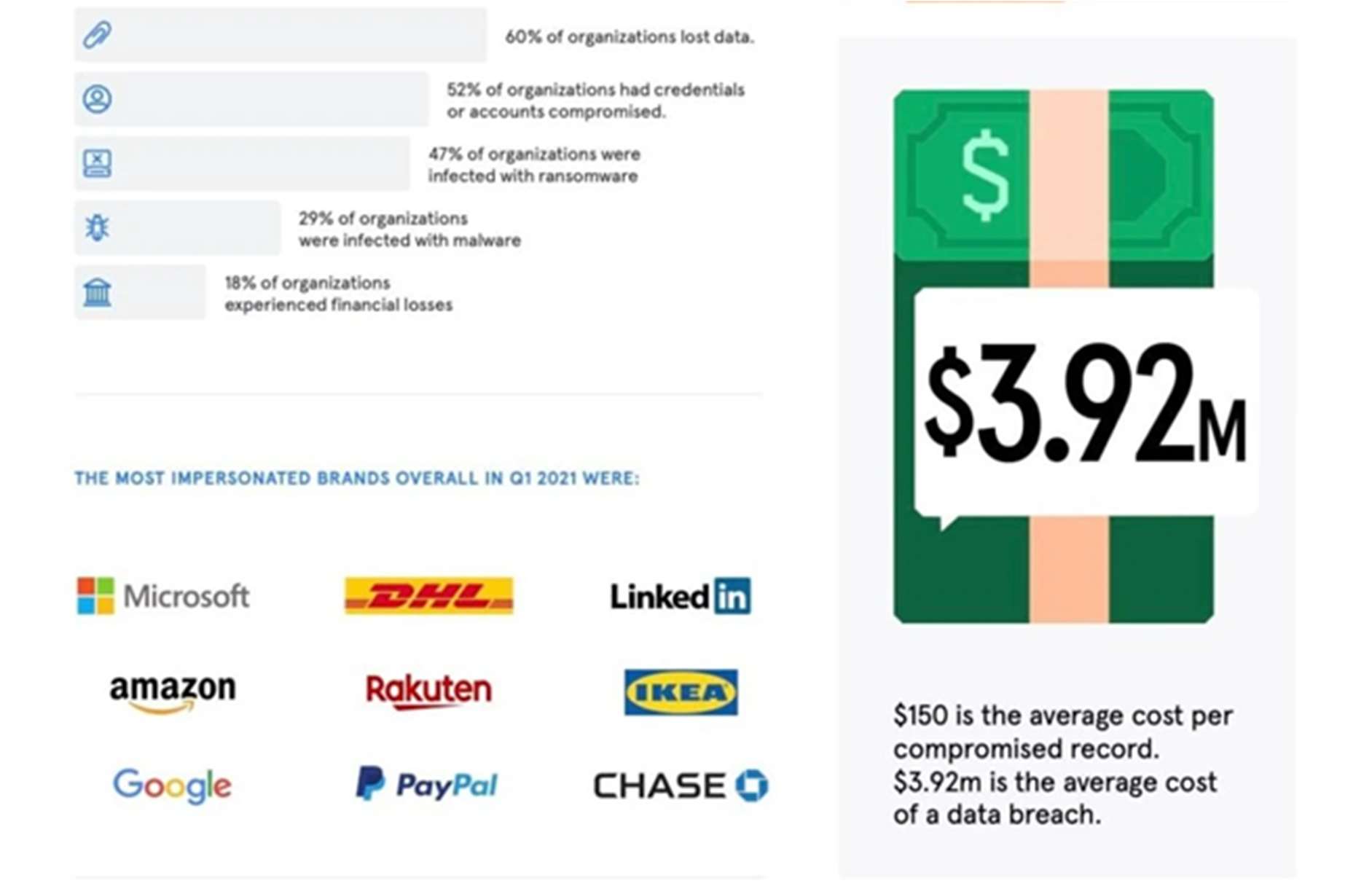
Source: IBM security Data breach report
The rise of hybrid work environments, expanding threats and a growing demand for flexibility and adaptability are leading organizations to invest on new Identity and Access Management (IAM) capabilities. According to a survey ran by Statista* in 2020 on over 300 organizations of 2000+ workers, 67% of CIOs were planning to increase investment on Password-less Authentication technologies in the coming years.
LEVELS OF SECURITY
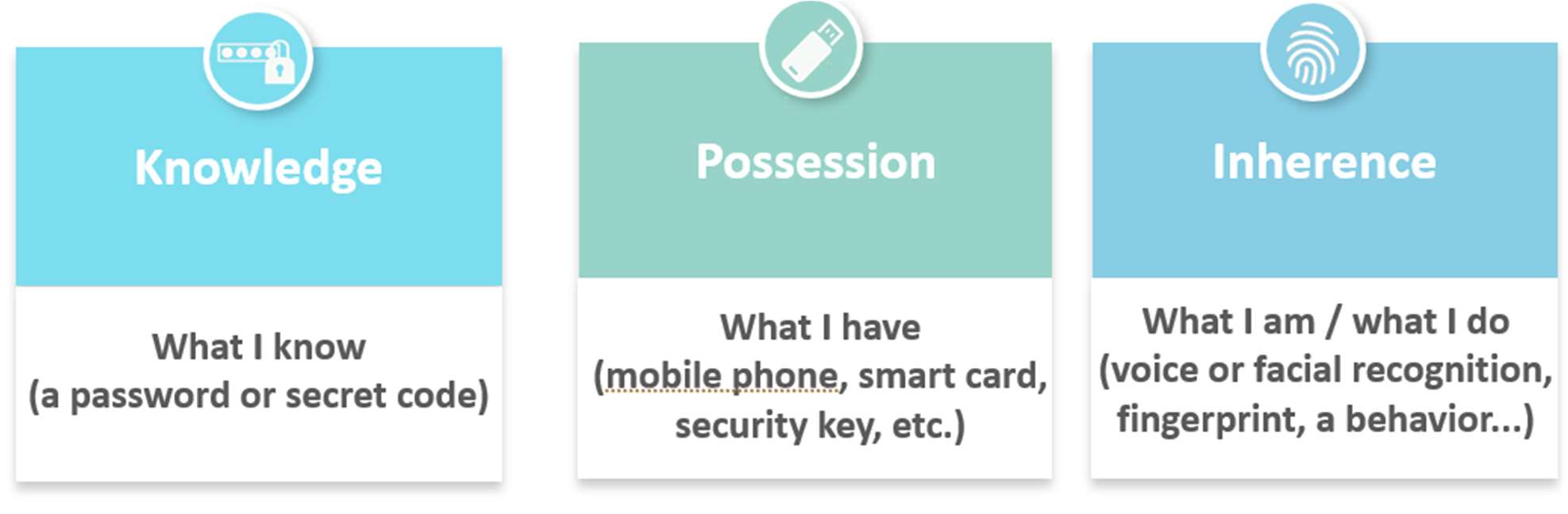
Simple authentication using a single factor such as a password is no longer sufficient. It shouldn’t be relied on as the only method to keep accounts safe as they are an easy target for hackers. Multifactor authentication, MFA, adds an additional layer of security to online services and accounts. This procedure consists of verifying the identity of the originator by the combination of at least 2 of the following 3 criteria:
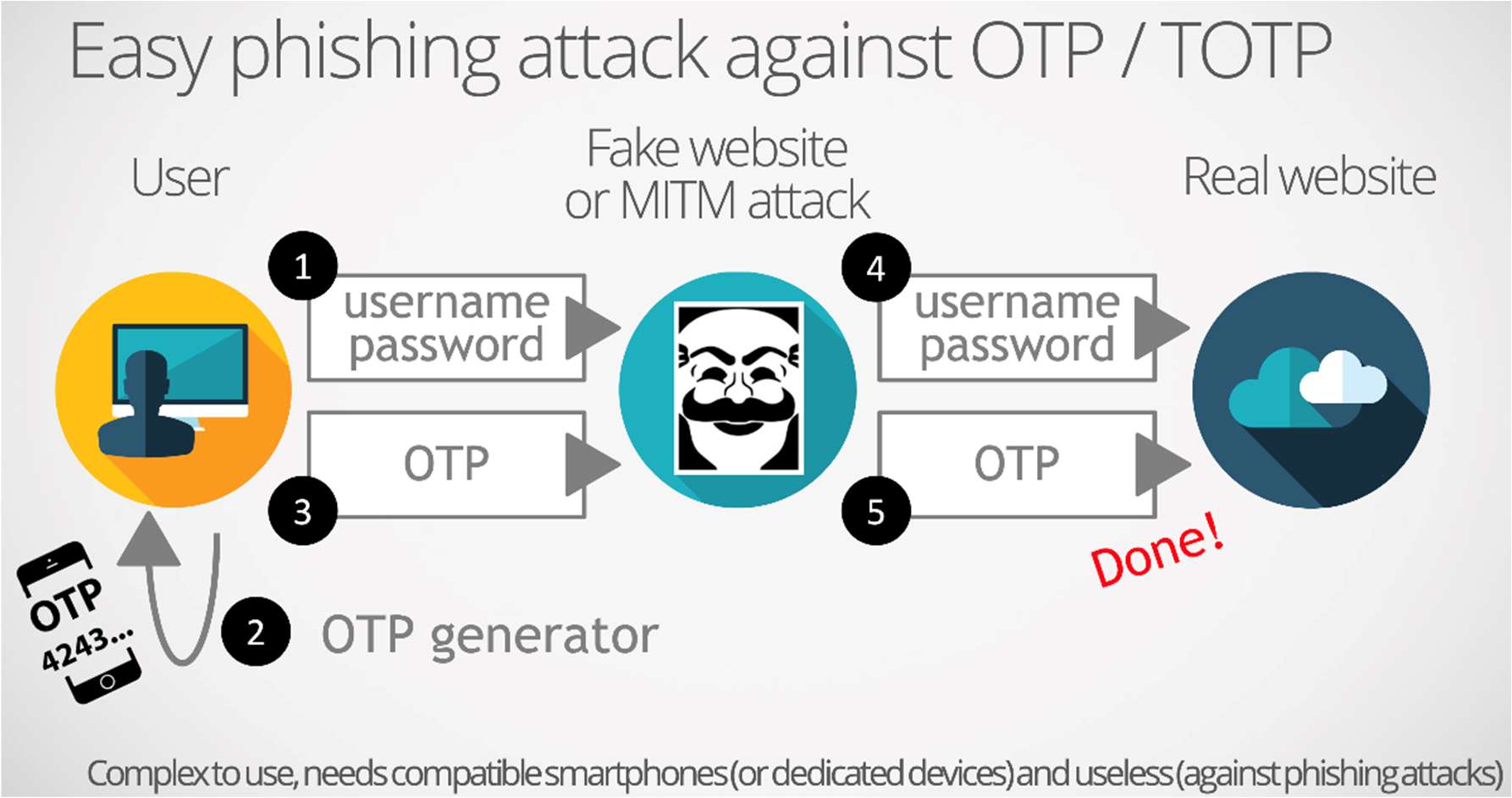
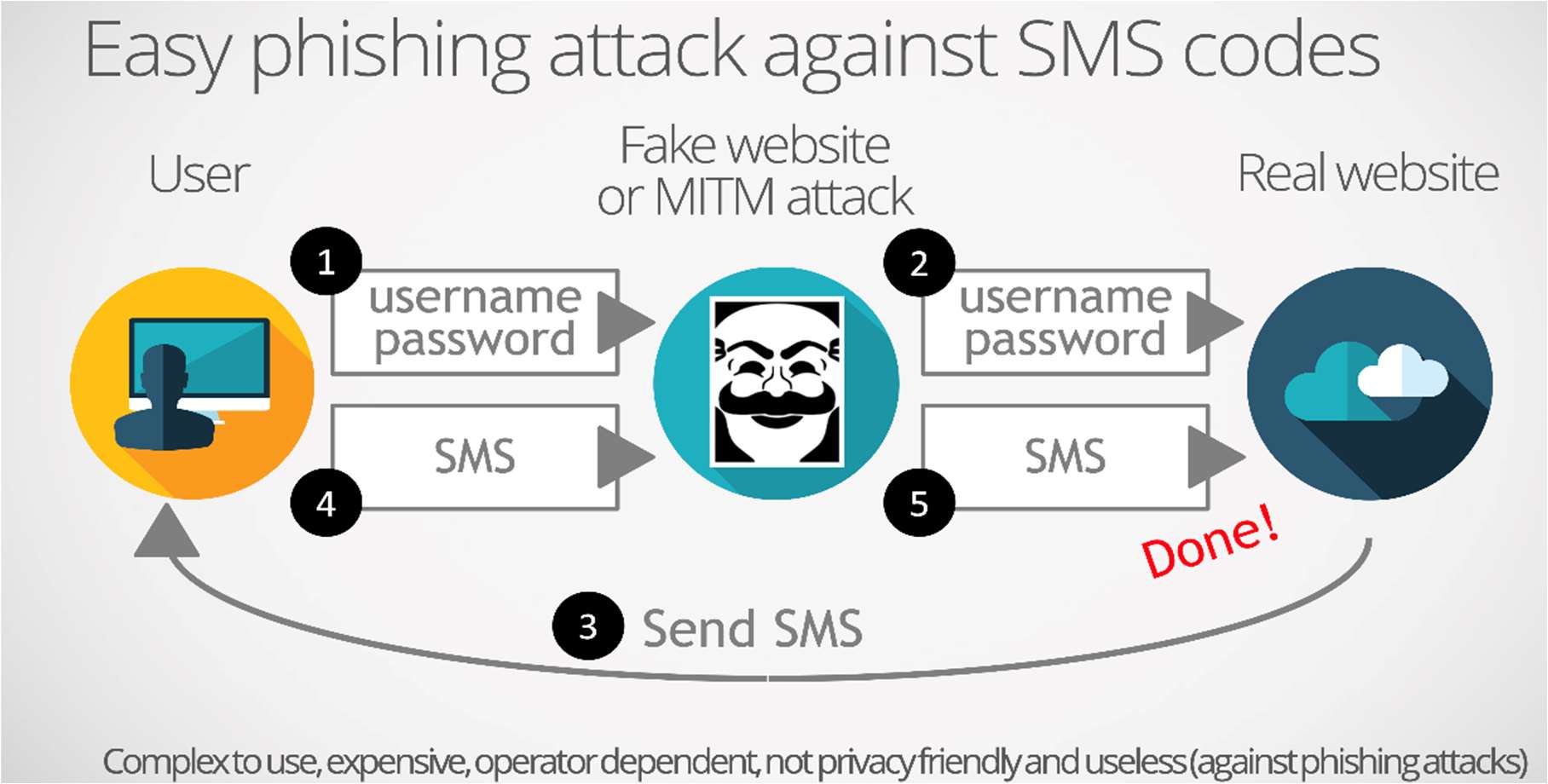
 The use of MFA tends to become widespread. More and more IT services are pushing or even imposing MFA (recently Salesforce, Whatsapp…). This method provides a step up in security but is not 100% effective against common threats like phishing and other advanced attacks. MFA does not constitute strong authentication. Attempts to strengthen sign in security with SMS transmitted codes and locally generated OTP codes have been shown to have vulnerabilities (text messages can be intercepted on the phone network and OTP codes relayed during ‘time-of-use » phishing attacks).
The use of MFA tends to become widespread. More and more IT services are pushing or even imposing MFA (recently Salesforce, Whatsapp…). This method provides a step up in security but is not 100% effective against common threats like phishing and other advanced attacks. MFA does not constitute strong authentication. Attempts to strengthen sign in security with SMS transmitted codes and locally generated OTP codes have been shown to have vulnerabilities (text messages can be intercepted on the phone network and OTP codes relayed during ‘time-of-use » phishing attacks).
STRONG AUTHENTICATION
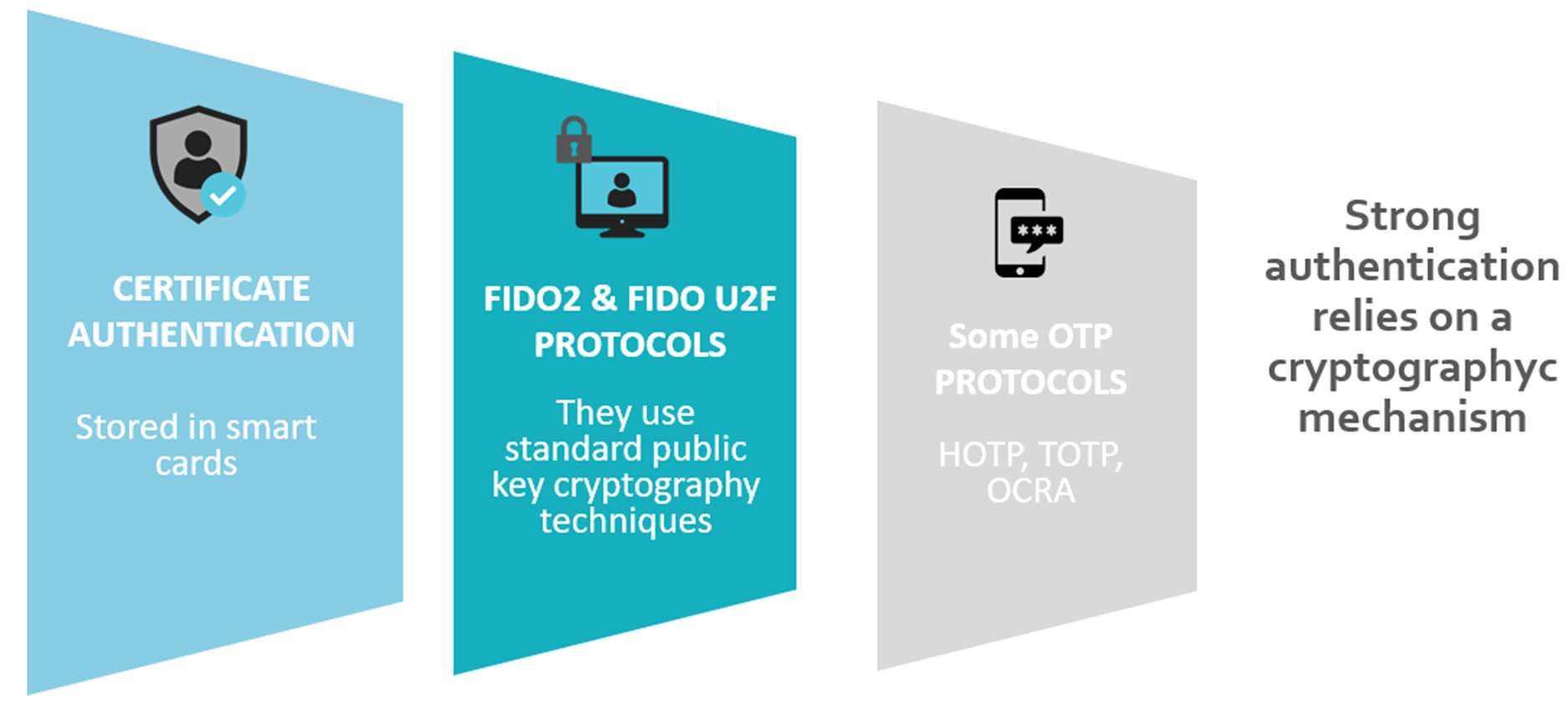
Strong authentication becomes essential when data or services are highly sensitive. It constitutes a phishing-resistant authentication. According to the the CNIL, Commission Nationale Informatique & Libertés, the French Data Protection Agency, in order to be considered strong, authentication must use a possession factor incorporating a qualified or certified safety component and be based on cryptographic mechanisms. The CNIL recommends favoring the use of strong authentication methods based on cryptographic mechanisms in accordance with the RGS (The French General Security Reference).
Among the examples of strong authentication listed by the CNIL: